Capturing Questionable Vote-By-Mail Requests from the Web
Voter Focus offers an optional feature to help detect fraudulent Vote-By-Mail requests submitted on your website through the Absentee/Mail Ballot Request Form. The requests are blocked from being processed into voter records, thus preventing the release of mail ballots to those intent upon voter fraud.
To use this feature, you run the Fraud Detection program, which scans requests from a specified time period, looking for those originating from the same IP address or having the same email address for ballot delivery. Requests whose addresses present no issue are passed to the Web Request Queue for processing into voter records. But questionable requests are detained for user review.
During your review, you can release a detained request to the Web Request Queue or you can put an indefinite hold on it. Where an address is known to be legitimate, you can set the Fraud Detection program to pass all requests associated with that address.
The Fraud Detection feature is under Vote By Mail > Vote-By-Mail Fraud Detection. To see this feature, your county must have this option selected:
VOTER FOCUS ADMIN > System Options > Vote By Mail > Use Vote-By-Mail Fraud Detection
And the user must have the permission:
VoteByMailFraudDetection
We recommend you run the Fraud Detection program and evaluate its findings on a daily basis.
The Fraud Detection program uses these parameters on the Vote-By-Mail Fraud Detection Parameters dialog to determine whether a request should be held for review:
Email Threshold—The number of requests having the same email address at which the program will begin capturing the requests. For example, if the threshold is 5, the program will pass the first four requests with this email address but will detain the fifth and all subsequent requests with this address.
IP Address Threshold—The number of requests having the same IP address at which the program will begin capturing the requests. As with the email threshold, the program will detain any request meeting or exceeding the threshold.
Date of First Web Request to be Analyzed—The date at which the program will begin evaluating web requests. This date must be at least a year in the past. The program will look at all requests submitted on this date and thereafter until today, including those that have already been processed into voter records.
The program checks all requests submitted on the website, beginning with the first request on the start date, placing a hold on any request exceeding the email or IP address threshold, except for those that have already been processed into voter records. It then presents the user with its findings, organized as a list of fraud cases, as shown in the screenshot below. Each case contains the web requests exceeding the threshold for a particular IP or email address.
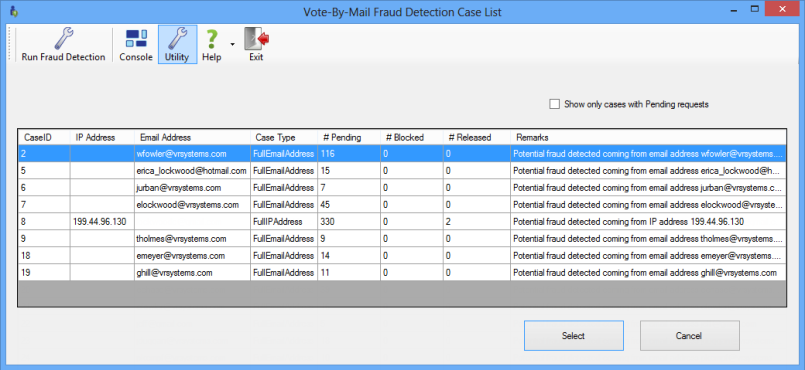
You can then open a case, examine its requests, and make determinations on individual requests within the case or a general determination on the case itself:
-
For individual requests, you can either release the request, block it, or leave it pending. A released request goes to the Web Request Queue where it can then be processed into the voter's record by the county user responsible for web request processing. Released requests continue to appear in the case list, as do requests that have been processed. If you don't want to see processed requests, you have the option of hiding them, so you can focus on requests that can still be acted upon.
-
For cases where the address is known to be legitimate, you can mark the address as approved, which releases all requests in the case to the Web Request Queue and allows any future requests associated with the address to be passed by the fraud detection program. Approving an address lets you pass requests from known locations, such as public libraries, where voters might use public computers to submit Vote-By-Mail requests.
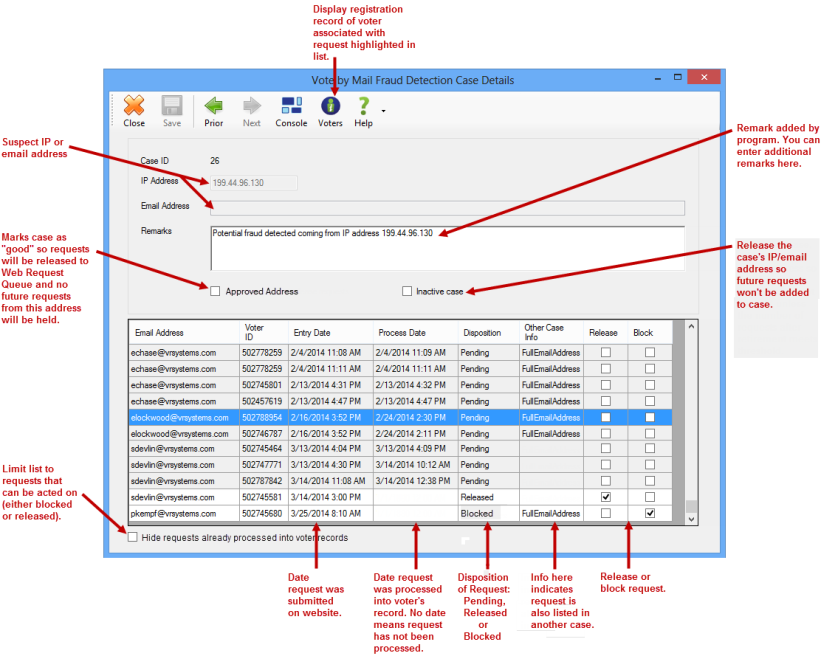
Web requests have one of three dispositions:
Pending—For counties using fraud detection, all web requests are assigned this disposition when they come into the Voter Focus system.
Released—This disposition is assigned by the user upon determination that the request is legitimate. It allows the request to enter the Web Request Queue for processing into the voter's record. Requests with the disposition Released will continue to appear in the case, even after they have been processed. If a county does not use fraud detection, all web requests are assigned the disposition Released.
Blocked—This disposition is assigned by the user upon determination that the request is fraudulent. It prevents entry of the request into the Web Request Queue. Should a Blocked request be reevaluated later as legitimate, it can be released by selecting the Release check box on the Vote By Mail Fraud Detection Case Details dialog.
If a request appears in more than one case and you change its disposition in one of those cases, the change will be reflected in the other case.
To run the Fraud Detection program, go to Vote By Mail > Vote-By-Mail Fraud Detection > Run Fraud Detection. During the run, if the programs finds new requests matching an existing case, it adds those requests to the case and displays a message indicating how many were added. If the program finds a new address meeting one of the prescribed thresholds, it will ask if you want to create a new case. If you say yes, the new case is added to the list of existing cases on the Vote-By-Mail Fraud Detection Case List dialog. If you say no, the requests associated with the suspect address will still be marked as Pending, even though a case has not been created. On subsequent runs of the program, if the same thresholds are used, you will be asked again if a new case should be created for those requests.
When counting the requests to meet one of the prescribed thresholds, the program does not consider whether a request has already been processed from the Web Request Queue into a voter's record. The first requests from an IP or email address that do not meet the threshold will not be stopped by the Fraud Detection program, so it is possible that a new case will contain requests that have already been processed, delivered, and perhaps even voted. (The same is true for requests processed before the county began using the fraud detection facility.) These requests cannot be "pulled back" or otherwise blocked by the Fraud Detection program.
The program does not evaluate the election for which a request is being made; requests for different elections can appear in a single case.
An all-elections request is considered a single request for the purpose of the Fraud Detection program.
In situations where an IP or email address is from a known legitimate source, you can mark the address as approved. This releases all requests in the case to the Web Request Queue unless a request appears in another case where the address is not approved. Approving an address allows any future requests associated with the address to be passed by the Fraud Detection program. To identify a case as good, select Approved Address on the Vote-By-Mail Fraud Detection Case Details dialog.
Note that if you select Approved Address and then clear this check box, the disposition of individual requests in the case will be reset to the settings in the last saved version of the case.
A case can be made inactive, which releases the once questionable IP or email address so that future requests with the address will be passed by the Fraud Detection program. This allows for situations where an internet service provider dynamically assigns a previously questionable IP address to a new, presumably legitimate location.
If you inactivate a case—by selecting Inactive Case and clicking Save on the Vote By Mail Fraud Detection Case Details dialog—the disposition of any requests in the case is essentially frozen. Inactive cases do not appear on the Vote-By-Mail Fraud Detection Case List, so the case itself can no longer be viewed and the disposition of requests in the case cannot be changed, unless they happen to appear in other, still active, cases.